Page 67 - 22.03.2021_IO1-CURRICULUM-FOR-VET-PROVIDERS_FINAL_plus-graphics
P. 67
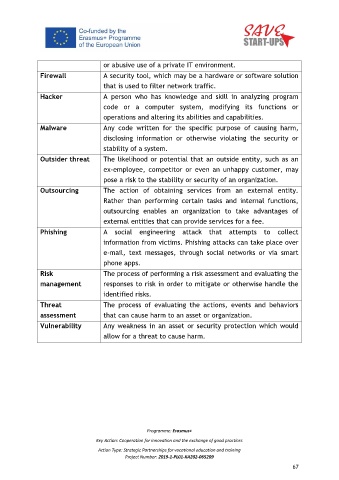
or abusive use of a private IT environment.
Firewall A security tool, which may be a hardware or software solution
that is used to filter network traffic.
Hacker A person who has knowledge and skill in analyzing program
code or a computer system, modifying its functions or
operations and altering its abilities and capabilities.
Malware Any code written for the specific purpose of causing harm,
disclosing information or otherwise violating the security or
stability of a system.
Outsider threat The likelihood or potential that an outside entity, such as an
ex-employee, competitor or even an unhappy customer, may
pose a risk to the stability or security of an organization.
Outsourcing The action of obtaining services from an external entity.
Rather than performing certain tasks and internal functions,
outsourcing enables an organization to take advantages of
external entities that can provide services for a fee.
Phishing A social engineering attack that attempts to collect
information from victims. Phishing attacks can take place over
e-mail, text messages, through social networks or via smart
phone apps.
Risk The process of performing a risk assessment and evaluating the
management responses to risk in order to mitigate or otherwise handle the
identified risks.
Threat The process of evaluating the actions, events and behaviors
assessment that can cause harm to an asset or organization.
Vulnerability Any weakness in an asset or security protection which would
allow for a threat to cause harm.
Programme: Erasmus+
Key Action: Cooperation for innovation and the exchange of good practices
Action Type: Strategic Partnerships for vocational education and training
Project Number: 2019-1-PL01-KA202-065209
67